How Many Steps Are in the Opsec Process
Psaki admits there are. FM 34-8-2 3-1 Chapter 3 MILITARY DECISION-MAKING PROCESS MDMP MDMP in General FM 101-5 is the doctrinal source.

Military Discipline In Industrial Control Opsec Incibe Cert
Data breaches often show up quickly on the dark web.

. Once a word or term becomes ingrained in the collective mindset it tends to stick. If you become a victim report the identity theft as soon as possible. It differs from a traditional con in that it is often one of many steps in a more complex fraud scheme.
Although cable TV regularly uses a digital video recorder many people still refer to the recording process as taping a throwback to the VHS days. When data brokers get hacked the stolen data can include compromised credit cards social security numbers and other data depending on what was exposed in the breach. The term social engineering as an act of psychological manipulation of a.
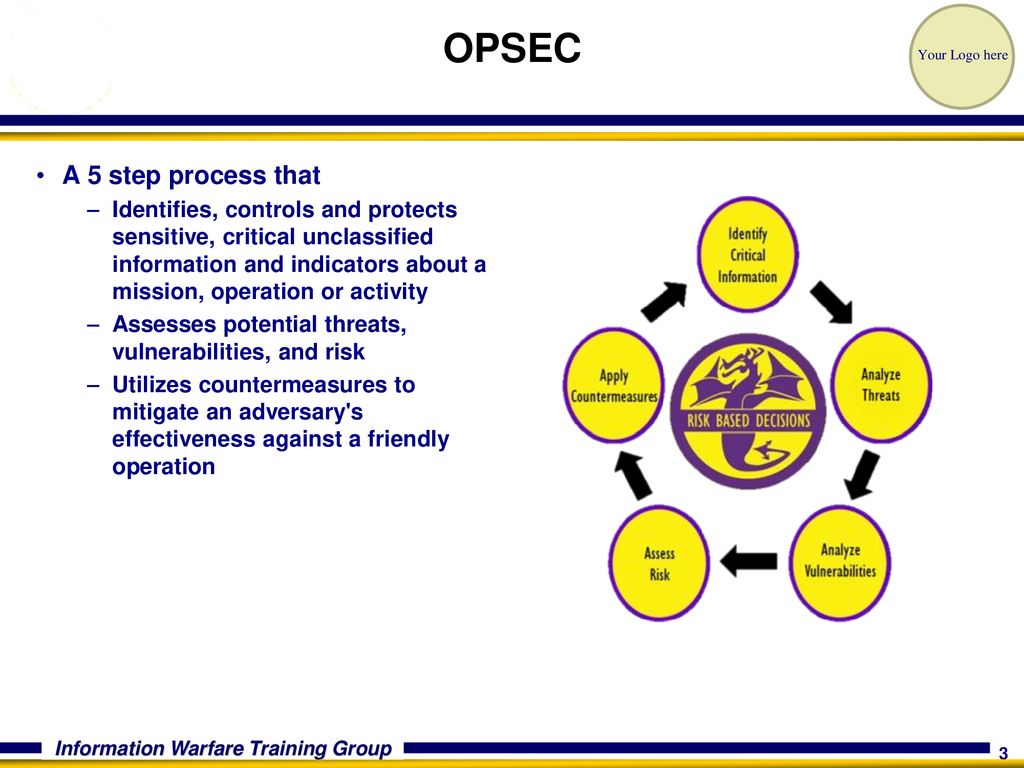
Secret airfield near Ukrainian border is getting 17 flights of weapons A DAY as West sends in 17000 anti-tank missiles. Which is a process that identifies critical information to determine if friendly actions can be observed by enemy intelligence. The MDMP is a single established and.
Confusion over the difference between virus and malware comes down to entrenched name recognition. This is a common way for identity theft and doxing attacks to occur.

Opsec Process 17 Identifying Critical Information In The First Step Download Scientific Diagram
Overview Opsec Threat Critical Information Indicators Data Aggregation Ppt Download
No comments for "How Many Steps Are in the Opsec Process"
Post a Comment